Want to run a business without technology? You’re in the wrong line of work; technology is so deeply ingrained in business that it’s not going anywhere. From your communication platform to your point-of-sale software, you need technology, and where there’s technology, there will inevitably be a need for technicians.
Global Tech Solutions Blog
Every day, cybercriminals wake up and choose violence.
Whether it’s a nasty strain of ransomware demanding a king’s ransom or a sneaky little virus that just wants to watch your business burn, the threats never stop coming. That’s why locking down your business is as essential as putting cream in your morning coffee.
How much time and money do you spend wrestling with your business’ software? Between updates, license renewals, and that one employee who keeps accidentally deleting their email app, it’s enough to make you want to scream. Unfortunately, software is kind of non-negotiable. You need it. So, should you go old school and buy it outright, or should you consider moving to the cloud and employing Software-as-a-Service?
With remote workers, you have a lot more questions to consider on a daily basis, especially in the realms of productivity and security. If you’re not careful, you could put your business at risk. Here’s how you can face these challenges head-on and ensure your organization doesn’t suffer any negative side effects of remote work.
In the interest of communicating how critical proper business cybersecurity is to manage, we’ve decided to take a different approach and put forth a scenario in the form of a daytime soap. As such, please feel free to read this post with dramatic music playing in the background and all dialogue imagined with elevated intensity.
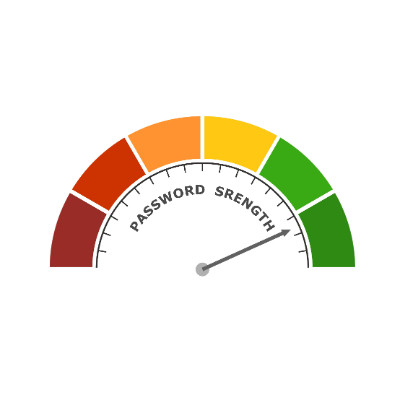
In the town of Oak Falls, life seems peaceful… but under the surface, tension persists. Secrets run amok, and with so much information to take in, everyone has to worry about the Strength of Our Passwords.
Two things are invariably true in the modern business landscape: technology will play an integral role in operations, and obtaining this technology will require a relationship with vendors and service providers. As such, anyone seeking to run a business successfully must interact with these external parties and enter into business contracts.
This needs to be handled carefully, so while we aren’t offering legal advice, you should follow a few practices before and during the negotiation of an IT contract.
Whether it’s a hard drive failure, a cyberattack, or just plain bad luck, losing data is a constant risk. Businesses and individuals alike suffer from data loss every day, and unfortunately, technology doesn’t always come with a safety net. Without a backup, you’re cooked if something bad happens. Today is World Backup Day! Let’s tell you why it is important to set up a reliable backup for your business.
How much data do your devices contain about your life? What would you do if law enforcement suddenly wanted access to it? Even if you’re a typical law-abiding citizen, you want to prioritize data privacy, but businesses also have an obligation to handle consumer information in a responsible way. Here’s what you need to know about law enforcement and access to your data.
Running a business is like juggling flaming torches while riding a unicycle, blindfolded. You’ve got employees, customers, operations, and, of course, vendors. Vendors keep the gears turning, but if you’re not careful, those relationships can turn into a never-ending headache that eats up your time, money, and possibly your sanity. So how do you make sure your vendors work for you, rather than the other way around? Here’s how to get the most out of them without losing your mind.
Technology drives today’s businesses; if you haven’t embraced modern technology, you’re missing out. So much of what used to make business frustrating can now be done conveniently through technology, including many old analog tasks. Today, we want to highlight some ways you can use technology to seriously upgrade your company’s operations.
Businesses rely on a ton of technology for their operations and, as such, rely on support to help keep these tools working effectively. We would know! We proudly provide our neighbors with the technical assistance they need to succeed. As we’ve done so, we’ve noticed that there are some support needs we frequently attend to.
Let’s review some of them and why they are so vital for you to have assistance in managing, preferably, from us!
We all have old friends; not the ones that you went to high school with, but oldish technology that we simply can’t bring ourselves to upgrade away from. At some point, however, old technology stops being a trusty sidekick and starts feeling like an anchor. If your devices are making life harder instead of easier, it might be time to say goodbye. Here’s how to know when it's time to let go and upgrade.
Skype is dead; long live Microsoft Teams.
At least, that’s the position that Microsoft has taken. The software company is discontinuing the two-decade-old communication application Skype, shifting focus to the more recent Teams platform, with the app’s last day being scheduled for May 5.
Let’s review what this means and reflect on Skype's impact on modern technology.
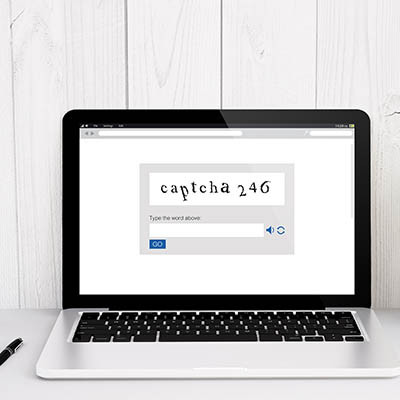
We’ve made it to the point where humans need to prove they’re real people to access systems, and one of the most common ways to do this is through the use of CAPTCHA technology. Completely Automated Public Turing test(s) to tell Computers and Humans Apart (try saying that with your mouth full) are everywhere, yet computers still struggle to actually crack these tests, unlike other methods of security. Why are they so successful at detecting automated bots?
We live in a moment in time defined by connectivity, which also means we live in a time defined by unwanted correspondence. It’s never been easier to reach you by phone, email, and even social media—even when you don’t want to be reached. Today, we’re talking about how social media, in particular, presents opportunities for scammers to target you and your loved ones.
Cybersecurity is one of those things everyone in a workplace should know about, no matter their role. But here’s the problem—turns out, a lot of people don’t.
A recent survey in the UK found that about one in three adults flunked a cybersecurity test. And get this—the test was designed for 11-year-olds. Yikes.
Business is filled with situations that can easily be turned into problems if they are not met with a proper solution. In some cases, it’s as simple as changing a course of action, but some problems are deep-rooted and need to be addressed aggressively. Technology can often be a business’ saving grace in such instances.
Let’s review some really bad scenarios that could be catastrophic, unless the right IT is in place.
Have you ever wondered how you can binge-watch Netflix, jam to Spotify, and accidentally fall into a three-hour Instagram scroll without your phone melting down? Thank the cloud for that. These apps don’t hoard all their data on your device—they store it online, so everything runs smoothly. And guess what? Businesses are using it too, because honestly, why wouldn’t they? Let’s take a look at some of the top benefits of the cloud.