With remote workers, you have a lot more questions to consider on a daily basis, especially in the realms of productivity and security. If you’re not careful, you could put your business at risk. Here’s how you can face these challenges head-on and ensure your organization doesn’t suffer any negative side effects of remote work.
Global Tech Solutions Blog
Have you ever thought about whether a hacker could secretly read your emails with your clients and coworkers? If you handle your own email system, it's really important to know about email encryption. Encryption helps keep your emails safe and private so you can focus on running your business without worrying about hackers.
Here are three big problems you could face if you don’t encrypt your emails:
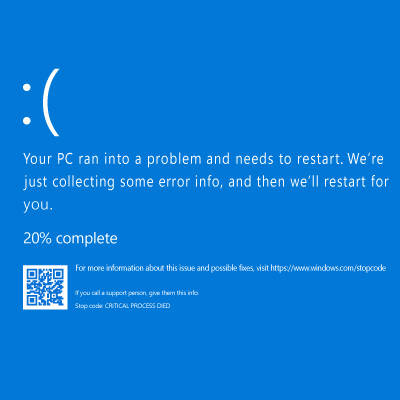
July 18th, 2024 saw one of the most widespread and devastating outages in recent memory, as a global update from cybersecurity company CrowdStrike brought about significant impacts to major infrastructures and societal needs. All this occurred even though only 1% of Windows operating systems experienced the issue.
Are you prioritizing your business’ network security? It’s remarkably important that any modern business focuses its efforts on this aspect of running a company. Still, it can be challenging to implement the right tools for the job—particularly if you are a future-minded business. You want to get the best return on your investment, which makes sense. Let’s help you get there.
Network security is complicated, and as such, you need to have considerable knowledge of it to ensure that your business is as secure as possible against the plethora of threats out there. Thankfully, you don’t have to do it alone. We want to give you some insight into the dos and don’ts of network security.
Email is complex, despite all appearances. It’s easy to overlook its complexities when you log into your account and it just works. However, you’ll need to ensure that your email is managed properly, as well as secured with protective measures for the underlying technology. Let’s go over some of the more effective methods you can use to keep your infrastructure secure from all types of threats, whether they are visible or hidden.
Does your business rely on the strength of its information systems? If so, you understand just how important cybersecurity is to the health of your organization. In a near-constant attempt to maintain organizational cybersecurity, many organizations have started changing the way that they approach data and network security, by moving their security efforts to the edge of their network. This is called edge security, and there are some very intriguing benefits.
Passwords, as annoying as they are sometimes, are the front line of defense to almost every account and profile your business depends on. That doesn’t stop security professionals from trying to develop better strategies to secure digital systems. Some of the biggest names in tech are searching for ways to forge ahead passwordless. Let’s take a look at one example that has drawn the attention of the tech community.
For quite a while it took an actual disaster to encourage business leaders to allocate any time and money to put towards cybersecurity. Many businesses still don’t, in fact. Those that have, while absolutely prudent in their use of resources to help ward off security problems, may forget that there are still things that need to be done aside from employee training to keep their security up. Let’s go through a few things that every organization should be doing to maintain the security of their information systems.
When dealing with business computing, there are many situations where threats could potentially ruin the good thing you’ve got going. Today, a lot of businesses are getting much more serious about their IT security with what is known as a “zero-trust policy”. What exactly is a zero-trust policy? This month we will explain it.
When it comes to your network and its security, you cannot give all of your users access to all of your assets. It’s just not a good practice, and doing so can potentially put your resources at risk. Let’s discuss how network segmentation can make a world of difference for the integrity of your network and the data found on it.
If Edgar Allan Poe worked in an office, here’s what one of his works would sound like:
True!—nervous—very, very dreadfully nervous I have been and am, but why will you say that I am mad? The office had sharpened my senses—not destroyed—not dulled them. Above all was my sense of hearing. I heard all things in heaven and on earth and many things in…the other place. So, how then am I mad, especially when I can so healthily and calmly tell you this story?
While we strongly recommend that you put the security safeguard known as multi-factor authentication in place wherever it is available, it is important that we acknowledge that cybercriminals are frustratingly inventive. So much so, in fact, that a new form of attack has been developed to take advantage of MFA, referred to as MFA fatigue.
Social engineering is a dangerous threat that could derail even the most prepared business. Even if you implement the best security solutions on the market, they mean nothing if a cybercriminal tricks you into acting impulsively. Let’s go over specific methods of social engineering that hackers might use to trick you.
Let me ask you a question… if you were a hacker, how quickly would you take advantage of newly disclosed bugs and other vulnerabilities? I’d bet it would be pretty quick, and industry experts agree. According to these experts, there’s less and less time for security professionals to react to vulnerabilities and zero-day threats… and it continues to shrink.
So, the question remains, how prepared is your business to respond when these kinds of vulnerabilities are taken advantage of?
Sometimes it can be easy to take cybersecurity for granted, especially when you consider that built-in security features are more powerful than they have ever been. Unfortunately, if you think that cybersecurity is something that ends with the built-in security of your desktops and laptops, then you’re in for a rude awakening.
Hacking attacks can be stressful to manage, but when you add in that they can strike when you least expect them to, it gets a lot worse. You’ll never know how you respond to such an event unless you simulate it and replicate it somehow. This is what the penetration test is used for; it provides your business with a way to prepare for cyberattacks.